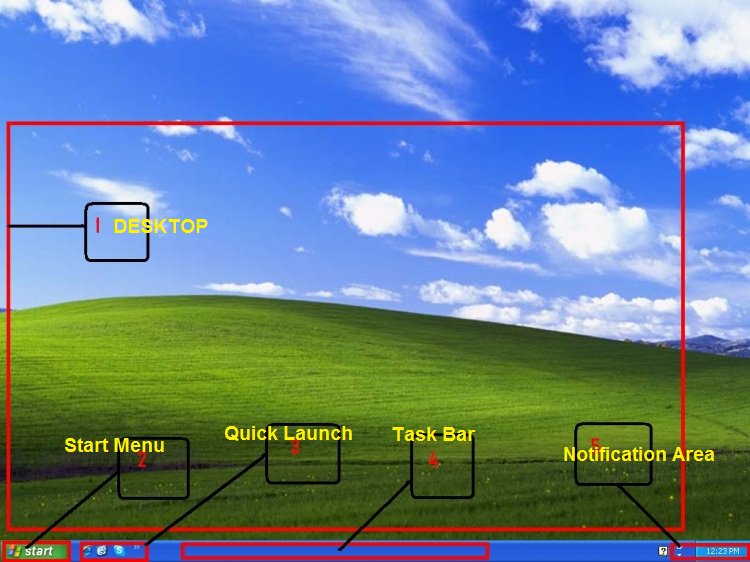
Question No 1: Marks 5
(a) The environment given in the snapshot will be quite familiar to you. Following image contains some components labeled with numbers. All these components are part of windows environment. Your task is to identify and name them.
Solution
1. Desktop
The large area that is the upper part of the screen is called the Desktop. Sometimes (to keep you confused!) people may use the term Desktop to refer to everything you see on the monitor after Windows has gotten started.
2. Start menu
We saw in the last lesson that the desktop can be used to launch your software. Another way to launch your programmes is through the Start menu at the bottom of the Desktop. Your Start button should look something like the one below.
3. Quick Launch
The Quick Launch toolbar, next to the Start Menu button, holds shortcuts to your frequently used programs. This is handy because the Taskbar is normally in view all the time. Desktop shortcuts can get hidden by open applications.
4. Taskbar
Across the bottom of the screen we see the Taskbar. Normally it is in view all the time. The Taskbar’s main job is to show what applications are currently running.
5. Notification Area
The notification area, or tray, at the far right of the Taskbar is used to show icons for programs that are awake and hanging around in the background, like the clock, anti-virus, and scheduling programs.
(b) Assume that you are working on your computer and your Mouse suddenly stopped working. How would you perform these tasks by using keyboard only? You are required to mention the keyboard short cuts of the following tasks.
1. To close a window.
Answer: I will press (ALT + F4) to close window
2. To cut a selected file/folder
Answer: I will press (Ctrl + X) to cut a selected file/folder
3. Window switching among open applications
Answer: I will press (Alt + Tab) for Window switching among open applications
4. To rename a selected file
Answer: I will press (F2) to rename a selected File
5. To open command prompt (DOS).
I will press windows key + r and then type cmd to open Command Prompt (DOS)
Question No 2: Marks 5
Internet is a great source of information. Your task is to find and learn the information available on internet about virus and its types. You are required to write in your own words about virus and its 4 different types.
Trojan Horse:
A trojan horse program has the appearance of having a useful and desired function. While it may advertise its activity after launching, this information is not apparent to the user beforehand. Secretly the program performs other, undesired functions. A Trojan Horse neither replicates nor copies itself, but causes damage or compromises the security of the computer. A Trojan Horse must be sent by someone or carried by another program and may arrive in the form of a joke program or software of some sort. The malicious functionality of a Trojan Horse may be anything undesirable for a computer user, including data destruction or compromising a system by providing a means for another computer to gain access, thus bypassing normal access controls.
Logic Bombs/Time Bombs:
These are viruses which are programmed to initiate at a specific date or when a specific event occurs. Some examples are a virus which deletes your photos on Halloween, or a virus which deletes a database table if a certain employee gets fired.
Worms:
A worm is a program that makes and facilitates the distribution of copies of itself; for example, from one disk drive to another, or by copying itself using email or another transport mechanism. The worm may do damage and compromise the security of the computer. It may arrive via exploitation of a system vulnerability or by clicking on an infected e-mail.
Rootkit Virus:
A rootkit virus is an undetectable virus which attempts to allow someone to gain control of a computer system. The term rootkit comes from the linux administrator root user. These viruses are usually installed by trojans and are normally disguised as operating system files.